F.A.Q
What is a BioGlyph?
When a user creates their personalized set of prompts, the authentication server stores this information in a secure manner. When the user needs to authenticate themselves in the future, the prompts are presented to them in a randomized order, and the user responds with their pre-registered interaction pattern for each prompt.
The authentication server then combines these patterns to create a multifactor digital signature that is unique to the user and can be used to authenticate them. This approach provides a high level of security since the user's interaction patterns are not easily guessable or replicable by an attacker.
The authentication server then combines these patterns to create a multifactor digital signature that is unique to the user and can be used to authenticate them. This approach provides a high level of security since the user's interaction patterns are not easily guessable or replicable by an attacker.
Why should I be concerned about weaponized AI?
In today's digital world, user authentication is a crucial aspect of our online lives. We use passwords, security questions, and other means to prove our identity and access our accounts, personal information, and sensitive data. However, with the rise of artificial intelligence (AI), a new threat has emerged: AI being weaponized to impersonate user authentication.
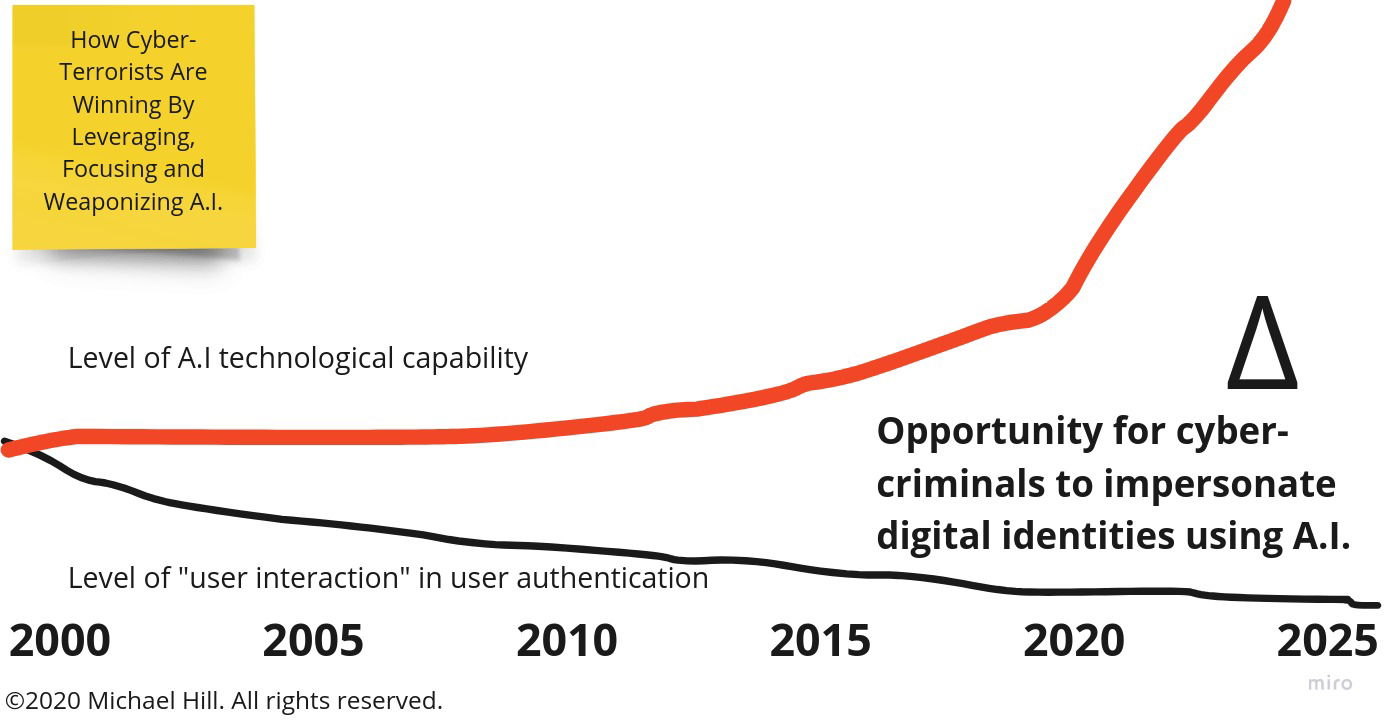 AI algorithms are designed to learn from data and mimic human behavior. This makes them highly effective at impersonating human users, as they can analyze patterns and replicate them in their interactions. For example, an AI-powered bot can easily mimic the way a human user types, clicks, and interacts with a website, making it difficult for the website to detect that the interaction is not coming from a human.
AI algorithms are designed to learn from data and mimic human behavior. This makes them highly effective at impersonating human users, as they can analyze patterns and replicate them in their interactions. For example, an AI-powered bot can easily mimic the way a human user types, clicks, and interacts with a website, making it difficult for the website to detect that the interaction is not coming from a human.
This is a concerning development, as it opens up the possibility of AI being used to carry out large-scale impersonation attacks on user authentication systems. This can lead to the theft of sensitive information, the manipulation of online transactions, and the compromise of user identities. In addition, the use of AI in impersonating user authentication can also lead to increased levels of automation in cybercrime, making it easier for attackers to carry out their crimes on a massive scale.
One of the major challenges with detecting AI-powered impersonation attacks is that AI algorithms can be highly sophisticated and adaptive, making it difficult to identify them using traditional security measures. This is why there is a growing need for new approaches to user authentication that can effectively detect AI impersonation attacks.
One such approach is the use of biometric technologies, such as fingerprint scanning, facial recognition, and iris scanning. These technologies use unique physiological or behavioral characteristics of an individual to identify them, making it much harder for an AI algorithm to impersonate them. For example, an AI algorithm may be able to replicate a password or security question, but it would be much more difficult to replicate the unique patterns in a person's fingerprint or iris.
Another approach is the use of cognitive authentication, which uses the power of the human mind to prove identity. This involves using unique mental processes and capabilities, such as memory recall and problem-solving, to identify an individual. Unlike traditional authentication methods, cognitive authentication is much more difficult for an AI algorithm to replicate, as it requires a level of human thought and understanding that is beyond the capabilities of AI.
In the end, the weaponization of AI in user impersonation is a growing concern in the digital world. It is essential that we adopt new and innovative approaches to user authentication that can effectively detect AI impersonation attacks and protect our sensitive information and identities. The fusing of biometric technologies and cognitive authentication, which utilize the unique and personal characteristics of the human mind, is a promising solution that has the potential to provide a more secure and reliable means of user authentication in the digital world. By using the power of our human minds, we can take back control of our digital identities and ensure that they are protected from the threat of AI impersonation attacks.
 AI algorithms are designed to learn from data and mimic human behavior. This makes them highly effective at impersonating human users, as they can analyze patterns and replicate them in their interactions. For example, an AI-powered bot can easily mimic the way a human user types, clicks, and interacts with a website, making it difficult for the website to detect that the interaction is not coming from a human.
AI algorithms are designed to learn from data and mimic human behavior. This makes them highly effective at impersonating human users, as they can analyze patterns and replicate them in their interactions. For example, an AI-powered bot can easily mimic the way a human user types, clicks, and interacts with a website, making it difficult for the website to detect that the interaction is not coming from a human.This is a concerning development, as it opens up the possibility of AI being used to carry out large-scale impersonation attacks on user authentication systems. This can lead to the theft of sensitive information, the manipulation of online transactions, and the compromise of user identities. In addition, the use of AI in impersonating user authentication can also lead to increased levels of automation in cybercrime, making it easier for attackers to carry out their crimes on a massive scale.
One of the major challenges with detecting AI-powered impersonation attacks is that AI algorithms can be highly sophisticated and adaptive, making it difficult to identify them using traditional security measures. This is why there is a growing need for new approaches to user authentication that can effectively detect AI impersonation attacks.
One such approach is the use of biometric technologies, such as fingerprint scanning, facial recognition, and iris scanning. These technologies use unique physiological or behavioral characteristics of an individual to identify them, making it much harder for an AI algorithm to impersonate them. For example, an AI algorithm may be able to replicate a password or security question, but it would be much more difficult to replicate the unique patterns in a person's fingerprint or iris.
Another approach is the use of cognitive authentication, which uses the power of the human mind to prove identity. This involves using unique mental processes and capabilities, such as memory recall and problem-solving, to identify an individual. Unlike traditional authentication methods, cognitive authentication is much more difficult for an AI algorithm to replicate, as it requires a level of human thought and understanding that is beyond the capabilities of AI.
In the end, the weaponization of AI in user impersonation is a growing concern in the digital world. It is essential that we adopt new and innovative approaches to user authentication that can effectively detect AI impersonation attacks and protect our sensitive information and identities. The fusing of biometric technologies and cognitive authentication, which utilize the unique and personal characteristics of the human mind, is a promising solution that has the potential to provide a more secure and reliable means of user authentication in the digital world. By using the power of our human minds, we can take back control of our digital identities and ensure that they are protected from the threat of AI impersonation attacks.
How does SensiPass support inclusivity and Web Accessibility Directive?
SensiPass offers a revolutionary approach to user authentication that is vital for promoting equality and accessibility in both privacy and security. This also grants ALL users greater control over their digital identity, regardless of their physiological capabilities and constraints.
By enabling every user their choice of both an operating environment with which they are both familiar and comfortable with, and to create a unique interactive process for them, all users will be able to securely and predictively control their digital privacy.
A fundamental value at SensiPass is the importance of empowering users to have greater control over their digital identities through a user-friendly and secure authentication process.
By enabling every user their choice of both an operating environment with which they are both familiar and comfortable with, and to create a unique interactive process for them, all users will be able to securely and predictively control their digital privacy.
A fundamental value at SensiPass is the importance of empowering users to have greater control over their digital identities through a user-friendly and secure authentication process.
SensiPass is user authentication. How can this have anything to do with video games?
SensiPass can benefit the gaming industry in several ways:
1. Increased security: SensiPass can provide a secure way to authenticate players, reducing the risk of account hijacking, fraud, and cheating.
2. Improved user experience: SensiPass eliminates the need for players to remember passwords, which can result in a smoother and more convenient user experience.
3. Reduced customer support costs: By reducing the number of password-related issues, SensiPass can help gaming companies reduce the amount of time and resources they need to devote to customer support.
4. Increased player engagement: By providing a more secure and convenient way to access their accounts, SensiPass can help increase player engagement and retention.
5. New revenue opportunities: SensiPass can open up new revenue opportunities for gaming companies, such as premium subscriptions or in-game purchases that are more secure and convenient for players to make.
6. Data protection: SensiPass can help gaming companies protect sensitive player data, such as payment information and game progress, which can enhance player trust and confidence in the platform.
1. Increased security: SensiPass can provide a secure way to authenticate players, reducing the risk of account hijacking, fraud, and cheating.
2. Improved user experience: SensiPass eliminates the need for players to remember passwords, which can result in a smoother and more convenient user experience.
3. Reduced customer support costs: By reducing the number of password-related issues, SensiPass can help gaming companies reduce the amount of time and resources they need to devote to customer support.
4. Increased player engagement: By providing a more secure and convenient way to access their accounts, SensiPass can help increase player engagement and retention.
5. New revenue opportunities: SensiPass can open up new revenue opportunities for gaming companies, such as premium subscriptions or in-game purchases that are more secure and convenient for players to make.
6. Data protection: SensiPass can help gaming companies protect sensitive player data, such as payment information and game progress, which can enhance player trust and confidence in the platform.
